Ever since “smart” medical devices have come out, there have been a great deal of vulnerabilities affecting them. Whether it is due to connection through IoT devices, or to the existence of multiple operating systems communicating with each other, medical devices are inherently insecure. Only recently has the FDA begun requiring medical device manufacturers to threat model their devices as a comprehensive check to see where the vulnerabilities and weaknesses can arise inside the architecture.
ThreatModeler was recently at an event held by Health Information Analysis Sharing Center (H-ISAC) and met with dozens of CISOs & CISSPs of various health care companies. It was shocking to learn that the majority of these high-ranking cybersecurity officials did not really understand what threat modeling is! Even though the FDA has made it mandatory for these manufacturers to use threat modeling to increase device security, it is bewildering that most of them have brushed this mandate under the rug.
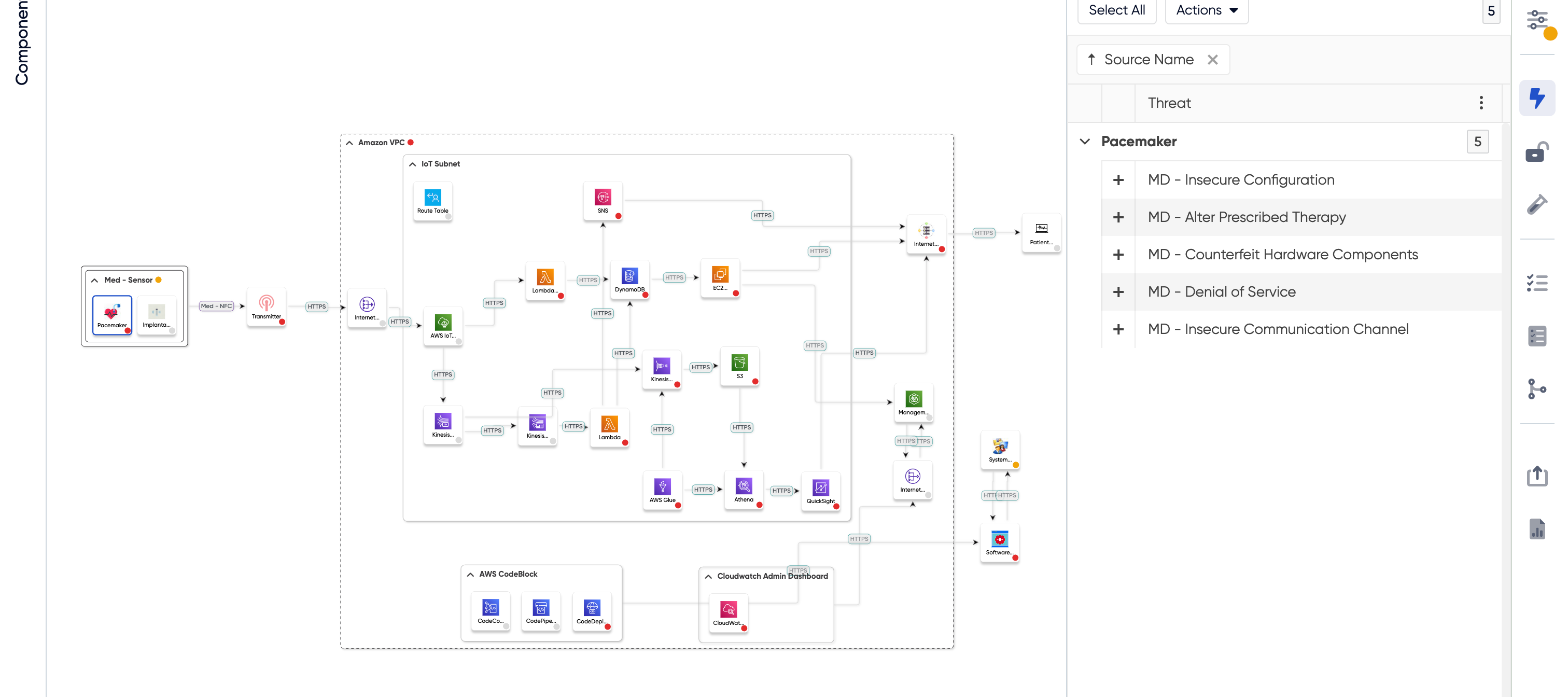
The problem arises with these companies simply diagramming their device/network/system architecture to just check a box. A diagram is beneficial but comes with many flaws. For example, people from the same security team can create vastly different diagrams for the same system/device. Security engineers must look at these diagrams and assign threats and security requirements to each individual section/component. If engineers miss mapping a threat or a security requirement, it could negatively affect the security of the device.
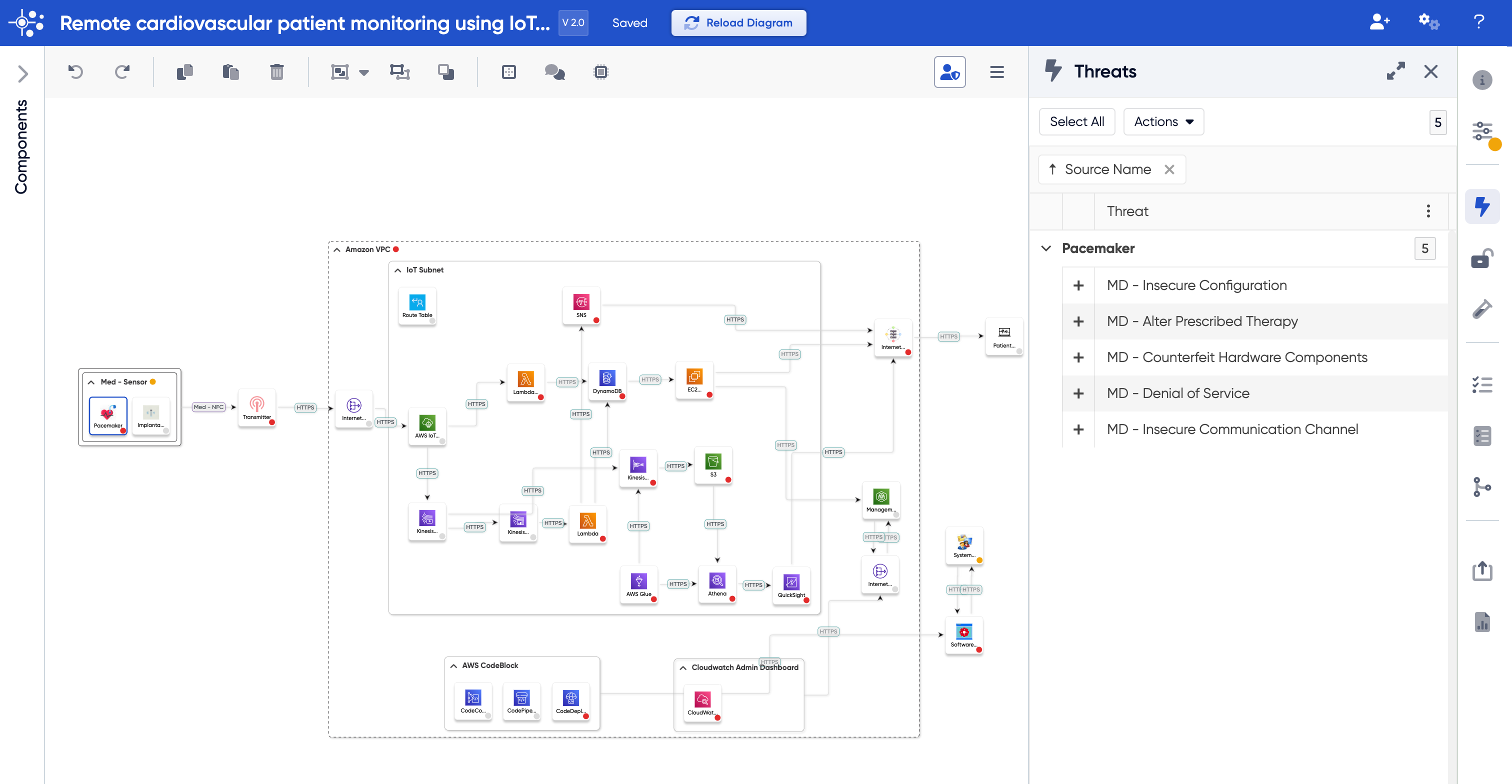
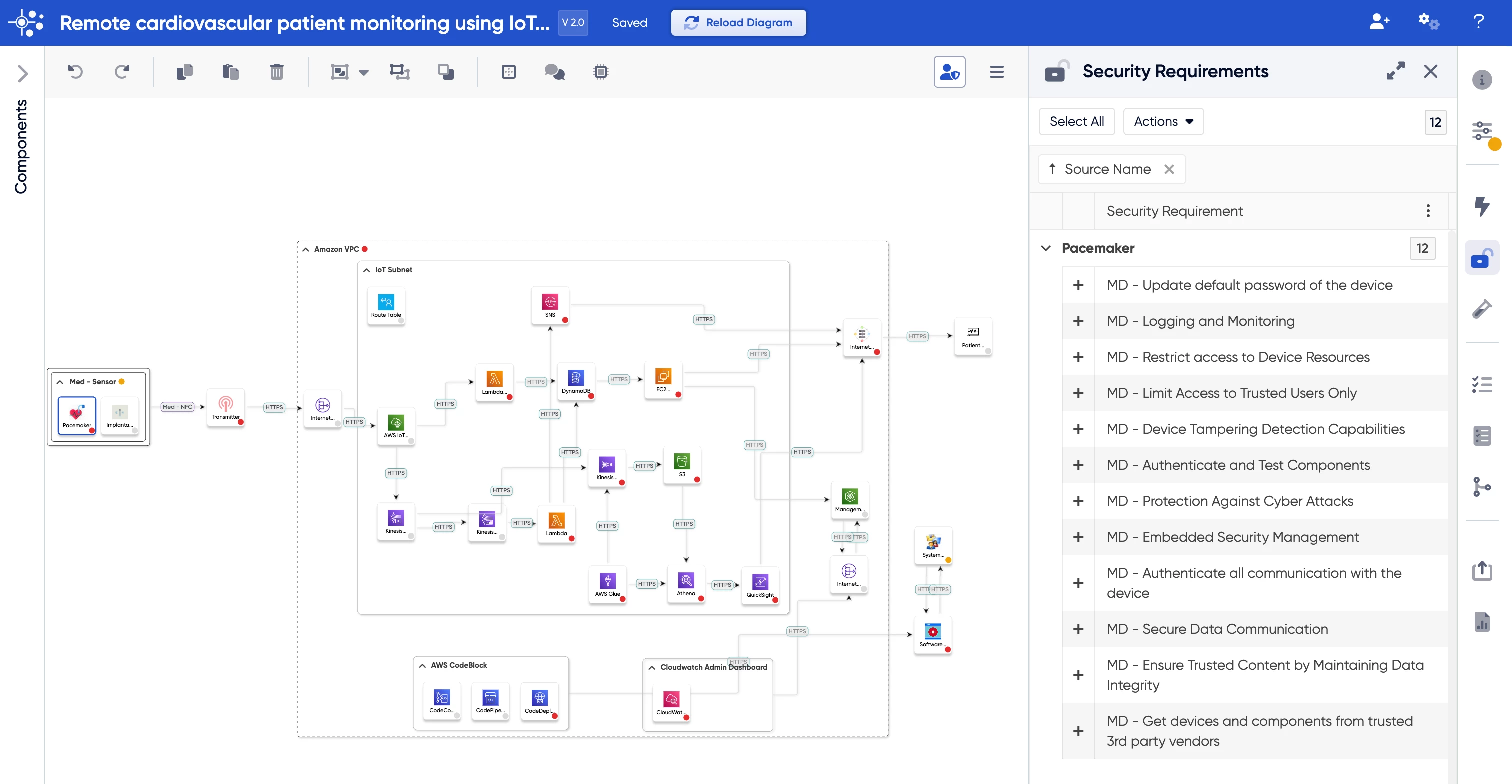
Comprehensive threat modeling negates all these issues. At ThreatModeler we have broken down devices/architectures into their individual components. These building blocks have threats and security requirements mapped to them, so when it is used in a diagram it brings those threats and mitigation strategies with it wherever it is used in the diagram. While the threat model itself may still look different from person to person, the threats and security requirements are standardized across the board.
This standardized threat model can be used by security professionals to visualize both the architecture of the system and the threats and security requirements that determine the model. While regular diagramming is limited in its capability, ThreatModeler enables you to identify threats in just two clicks, allowing you to make informed decisions for threat mitigation.
If the FDA considers threat modeling medical devices to be mandatory, simply diagraming architectures does not sufficiently improve the security of these devices. What is the point of enforcing low level diagrams if all the security risks are still there? To ensure security of these medical devices, comprehensive threat modeling should be mandatory.
Further reading: https://threatmodeler.com/why-medical-devices-need-to-be-secured-right-from-design/